Labels: Give Away, Google, Google Wave, Orkut, Social network
You can call this as a simpleton's viewpoint of technologies that are discussed here or the information that I share. I encourage discussion, so that more information can be gained, shared and made easy to understand, in the simplest way! I always look forward to people who (knowingly or unknowingly) practice 'Occam's razor'.
I've been tweeting for a pretty long time. The most useful twitter app I found was TweetDeck. I had to refresh the site periodically, which made me feel unconfortable. Then I remembered reading somewhere that Adobe Air applications are platform independent (correct me if i am wrong). Now, it occured to me that why not install TweetDeck in Ubuntu, as I work on GNU/Linux more than windows now a days. Given below is a step by step procedure of installing TweetDeck in Ubuntu.
(Please note that sentences highlighted with green color are commands that are to be executed in terminal.)
Phase 1:
Installing Adobe Air:
1. wget http://airdownload.adobe.com/air/lin/download/1.5/AdobeAIRInstaller.bin
2. Save the file in Home Directory, with the file name AdobeAIRInstaller.bin
3. chmod +x AdobeAIRInstaller.bin
4. sudo ./AdobeAIRInstaller.bin
5. The normal installer will now start. Install it. From now on, download any file with .air extension and double-click it to install.
Phase 2
Installing TweetDeck
1. Go to http://tweetdeck.com/beta/download/ and download the latest version of TweetDeck.
2. Save the file and double-click to run it.
Install it and Tweet on..!!
Labels: Gnu/Linux, Installation, TweetDeck, Twitter, Ubuntu

Labels: .NET Framework, Computer programming, Java, JavaScript, MySQL, PHP, Programming
Its that time of the year again when brains from all over theAsia meet each other face2face, compete with all their programming and problem solving skills in C , C++ and Java.. Yes..!! You guessed it right.. its ICPC time again atAmrita University..!!
Welcome to ACM International Collegiate Programming Contest 2009 Asia Regionals, the multitier, team-based, programming competition operating under the auspices of ACM and headquartered at Baylor University.
ACM ICPC 2009 Asia Regionals - Online Contest over internet will be held at Amrita University,Kerala.
Each team will consist of 3 members, all undergraduate, and they will be asked to solve a set of 8-10 programming challenge problems - mostly based on algorithms, within a period of 4 hours.!! The choice of programming language between Java, C++ and C is upto the team.
How to register????
A team can only compete in ACM ICPC 2009 Asia Regionals, if-n-only-if they've registered for the same. So, register here
Registration is for one team, consisting of 3 contestants and one coach. The “coach” refers to any full time faculty member of the university or institution, where the contestants pursue their studies.
The contest rules can be found here: Rules_ACM_ICPC09
Hurry up!!! Last date for registration is: 9 September 2009.
Contestant Feedback of the previous contests:
http://sathyaphoenix.wordpress.com/2008/12/09/acm-icpc-asia-regionals-amrita-university-kerala/
http://amritaicpc.wordpress.com/
For more info, visit http://icpc.amrita.ac.in/site/
Labels: ACM, ACM International Collegiate Programming Contest, Association for Computing Machinery, Baylor University, C++, Competition, Computer programming, Contests, Java, Kerala, Programming
2. Thou shalt not capitalize statements such as the "if" or the "for".
3. CONSTANTS shall be shouted to the multitudes in all caps, from every rooftop and steeple, as they are the unchanging firmament and change not through all time, and woe be to those that confuse them with variables.
4. Those Types and Structures which are user defined shall be presented with the first letter capitalized, as they are the high born, lest they be confused with the lesser variables, nor with the shouted CONSTANTS.
5. Variables shall be lower case, even as they start a sentence, for they are the low and common peasant workers doing the everyday drudgery of programming work, and must not be confused with the high-born Structures, nor with the ever-stable firmament of CONSTANTS.
6. Brothers have come to blows o'er the use of long variable names, with many favoring the internal capitalization, thus the use of
whereas others have countered with heated words that the proper way would be
long int number_of_people_in_hell;
Woe be to those who use either name, for it is likely not unique in the first six to eight letters, making some compilers gnash their teeth, while the true scope of the number of people in hell would vastly exceed the capacity of the long int, causing the dreaded plague which infecteth, locketh-up and rebooteth all computers from the lowly PIC to the mighty Cray.
7. While much blood has been shed over the issue of the curly brace, and many are the programmers that have argued that opening curly braces should go on their own line, while others have protested with sword-in-hand that they must go on the same line as the statement, and many have come to blows over this, the closing curly brace shall be indented to the same level as the opening function.
8. Thou shalt not comment the obvious. Those rapscallions and heathens who penned the line:
i++; /* Add one to i */
shall be forever banned from the inner circle of C, though their resume grow long and their accomplishments and finished code stretch out before them like a lake of ASCII text. Likewise, any code which is not obvious, or obfuscates and bebothers the user, shall be extensively commented so as to make clear the intent of the programmer.
9. Thou shalt comment the author, date, and revision of each C program, and lo, other comments shall be brief, descriptive, to the point, yet clear as the purest mountain spring water in their explanation and clarification of the code. Each function shall have as its companion a description of its function, its inputs and outputs, as each dog has its day and each actor his moment on the stage. Thou shalt document the purpose of each and every I/O pin in an embedded processor, and for each variable, data member or Structure there shall be a comment which shall illuminate and enlighten the reader of the program as to its use.
10. Thou shalt properly indent programs, each subservient function being indented one level more than its master.
courtesy: Suhas Kurup M
Lecturer, Dept. of Information Technology
Amrita Vishwa Vidyapeetham
Amritapuri Campus.
Kollam-690525
homepage: SuhasKurupM
Labels: ASCII, C Programming, Capitalization, Languages, Programming, Variable
Twitter is used for many purposes, including:
• Sharing interesting web links
• Reporting local news you have witnessed
• Rebroadcasting fresh information you have received
• Philosophizing
• Making brief, directed commentaries to another person
• Emoting and venting
• Recording behavior, such as a change in location or eating habits
• Posing a question
• Rickrolling (http://en.wikipedia.org/wiki/Rickrolling)
• Crowdsourcing
• Organizing flash mobs and tweetups (in-person meetups with Twitter friends
The Twitter culture has created its own lexicon, filled with new words you should
know. Here are a few of the basics:
Tweet: The preferred name for a status update.
Retweet: The reposting of an interesting tweet from another twitterer.
Detweet: Craig Danuloff suggests there should be a way to refute someone’s post by passing
along a tweet with “a degree of disapproval” (Sad part is tht we have Like in Facebook and don't have an option for Dislike.).
Tweeple/tweeps: Twitter people, Twitter members, Twitter users, twitterers.
Twoosh: A tweet that is a perfect 140 characters long.
Tweetup: When tweeple meet in person.
For a more complete list of Twitter words, try Twittonary, the Twictionary wiki , or the Twitter Fan Wiki’s Twitter Glossary.
Labels: Micro-blogging, On the Web, Online Communities, Social network, Twitter, Wiki
Now to install some themes..
Plan A
Go to Settings -> Options -> Personal Stuff -> Get Themes
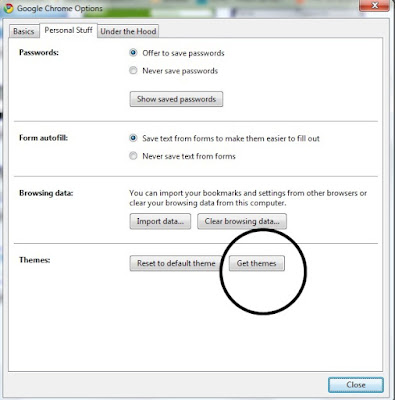
You'll be directed to the Google Chrome Themes Page .
Plan B
Go to https://tools.google.com/chrome/intl/en/themes/index.html and try out one by one. Save them in one folder.
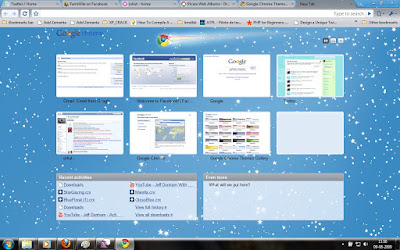
Sad that Chrome does not provide any kind of option such as Theme Selector. If you need to change the current theme, then you'll have to double click on the theme file you've downloaded, and thats where we find Firefox as a better option..!!
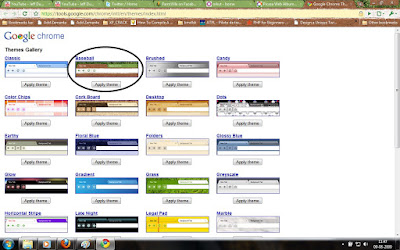
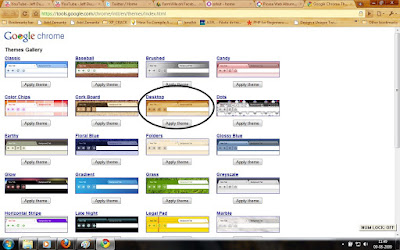
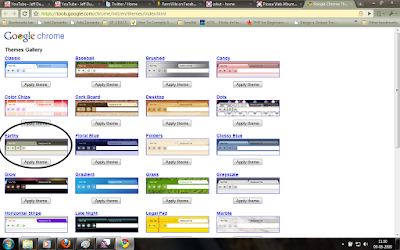
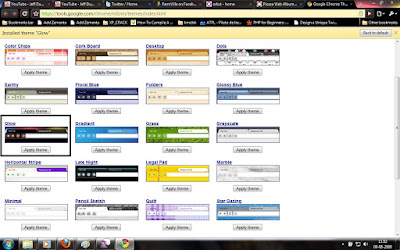
For me, some of the themes were so bright(Vertical Stripe , Legal Pad , Color Chips) and some were so pleasing. Anyway, its time for you people to try the new look for your chrome. Here are the screen shots of some themes which i like.
Baseball
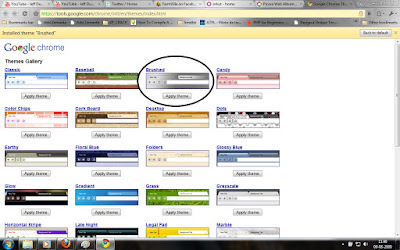
Brushed
Cork Board
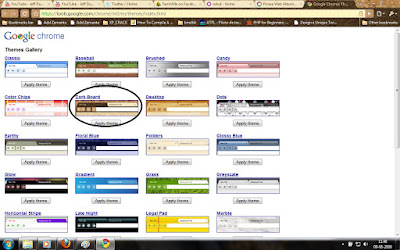
Desktop
Earthy
Glow
Floral Blue
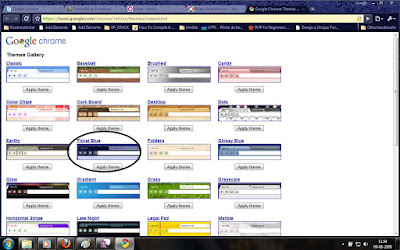
Grass
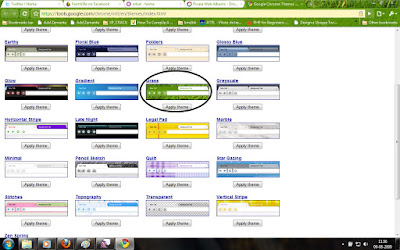
Stargazer
Zen Spring
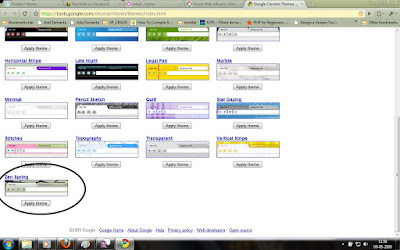
Minimal
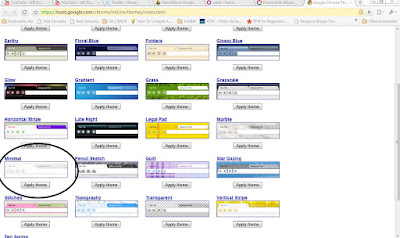
So wat are you waiting for?? Get a new look for your Chrome..!!
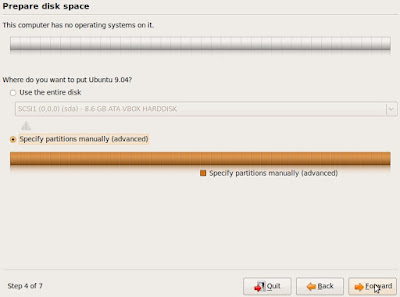
Labels: Ext3, Gnu/Linux, Grub, Linux, Linux installation, Mount, Opensource technologies, Ubuntu, Ubuntu 9.04, Ubuntu 9.04 installation, Ubuntu installation
Sometimes it may occur that you may hide those folders containing your "precious" files, and at the time when you need them..... BAM... u can't restore the hidden folder. Don't panic, its just the doing of USBWorm (Heap 41a).
W32.USB Worm or Heap41a attempts to periodically copy itself to removable drives and USB keys. The worm will attempt to create a hidden file Autorun.inf on the removeable drive and copy itself to the removeable drive as MicrosoftPowerPoint.exe. It will monitor internet brwser activities and display the following messages:
· “USE INTERNET EXPLORER YOU DOPE, I DNT HATE MOZILLA BUT USE IE OR ELSE…”
· “Orkut is BANNED you fool, The adminstrators didn’t write this program guess who did??”
And now, coming back to the solution to the “Hidden Folder problem”. Perform the following rituals.
1. Go to your Start menu, click on Run and open up your Registry Editor by typing "regedit" without the quotes and pressing OK.
2. Once there go to: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folde r\Hidden\SHOWALL
3. Delete the value CheckedValue. (Its type should be REG_SZ and data should be 2.)
4. Create a new DWORD value called CheckedValue (same as above, except that the type is REG_DWORD) by right clicking on the right pane->New->DWORD Value. Modify the value data to 1 (0x00000001).
Labels: Graphic Drivers, Info
Venu with his Gmail stickers

The Gmail Stickers..

Labels: Gmail Stickers
( For people who still have problem installing Daemon Tools, try installing Virtual Clone Drive. It seems Daemon Tools dont have support for beta editions.)
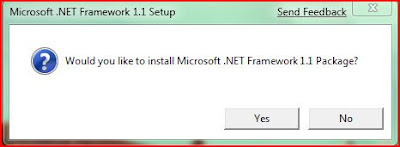
The next problem arose when I tried to install dotnet framework 1.1. When I tried doing that, the following error showed up.


 If user click “OK’, the installation of .NET 1.1 will be cancelled, while clicking “CANCEL”
If user click “OK’, the installation of .NET 1.1 will be cancelled, while clicking “CANCEL”produces another error message similar to below:
cardbg.exe !a 9×8e
Microsoft .NET Framework 1.1 SP1(Service Pack 1) has resolved the issue. However, Microsoft does not provide download to standalone .NET Framework 1.1 installer that integrated with SP1.
To fix this, we need to follow the following steps, which is called slipstreaming. We need to sliptstream .NET Framework 1.1 SP1 into .NET Framework 1.1 installer, so that both the .NET
Framework and the Service Pack can be installed at the same time.
Follow these steps:
1. Create a new folder named DotNet in C:\ drive. (The path i used was C:\DotNet )
2. Download Microsoft .NET Framework 1.1 Redistributable Package (dotnetfx.exe). Make
sure the setup file is saved as dotnetfx.exe.
3. Download Microsoft .NET Framework 1.1 Service Pack 1 (NDP1.1sp1-KB867460-
X86.exe). Rename the file to dotnetfxsp1.exe.
4. Copy both installation files into the same directory (i.e. C:\DotNet),.
5. Open Command Prompt as Administrator.
6. Change to the directory where the two installation files are stored, ie C:\DotNet.
7. Run the following commands one by one.
--> msiexec.exe /a c:\DotNet\netfx.msi /p c:\DotNet\netfxsp.msp
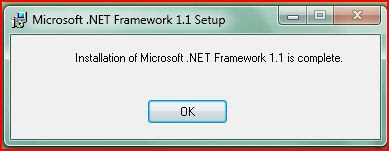
 Wait for the installer to disappear automatically.
Wait for the installer to disappear automatically.Dotnet Framework 1.1 is successfully installed. :-)

















